Text/ huawei distributed storage data security architect ren Yunqing
"Security" has always been a topic of concern to all mankind. Life security enables us to live and work in peace and contentment, while data security enables the digital economy era to operate smoothly. However, blackmail incidents still emerge one after another in the digital world, which threatens the development of all walks of life.
According to third-party statistics, up to 35.83 million ransomware attacks occurred in the whole network in 2022, an increase of more than 13 million times compared with 2021. There is no lack of large-scale vicious blackmail incidents.
Let's first find out what ransomware is. Ransomware, also known as ransomware, is a special malware, the biggest difference from other viruses is that the attack means are accompanied by targeted and organized network threat attacks and encrypted data behaviors aimed at ransom.
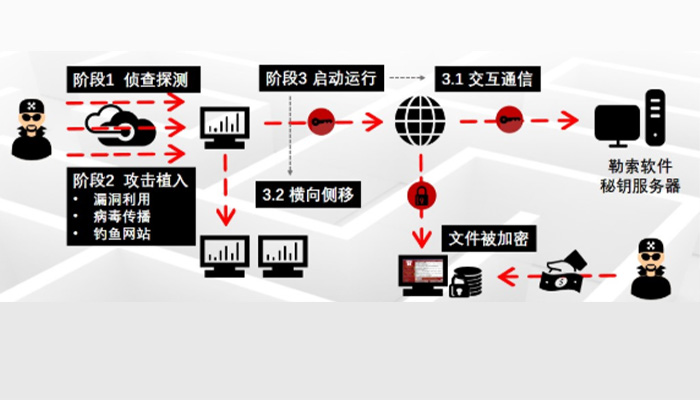
The attack process of ransomware usually has the following stages:
1. Investigation and Detection (investigation stage)
at this stage, attackers detect the target hosts in the Internet, such as active vulnerability scanning, and find out which hosts have unfixed vulnerabilities that can be exploited by ransomware. Once a vulnerability is detected, the attack starts.
2. Attack implantation (Transmission Stage)
at this stage, attackers may send virus-containing emails or phishing websites to targeted email addresses or other facilities, or exploit vulnerabilities discovered by scanning, A ransomware virus is implanted into the target production host or storage system.
3. Start running (side shift and encryption phase)
1) after the Blackmail virus is successfully implanted, it will start to run, obtain the key of the encrypted file from the attacker's blackmail software key server, and detect the network of the target to move horizontally, spread ransomware to as many hosts as possible. Some ransomware viruses with "double ransomware" mode also upload the key data of the target to the attacker's server. This phase has no significant impact on the service usage of the target and is not easy to detect.
2) when the Blackmail virus obtains the encryption key and spreads it, it encrypts the files that the host can access (including local files and mounted files in network storage) on a large scale. Some advanced ransomware viruses can also detect backup data in storage systems and actively delete backup data to prevent attack targets from recovering.
After the blackmail is implemented, an obvious prompt will be given to the target to ask for ransom.
Traditional network security solutions are mainly used for detection and dissemination. With telecommuting, mobile terminal access, supply chain ecosystem docking, and business cloud migration, enterprise boundaries have become increasingly blurred. The entire IT architecture has no single and easy-to-identify boundaries, as a result, border-based network security and data security face more and more challenges when formulating strategies, because once network threat attacks such as ransomware break through the border, horizontal movement will be unimpeded. In the face of blackmail virus attacks, on the one hand, it is necessary to improve the protection capability on the network side and reduce the possibility of being breached; On the other hand, it is necessary to improve the resilience of data security. When the network side leaks, it can do the following:
1) effectively prevent data from being encrypted;
2) timely warning of ransomware attacks;
3) after data is encrypted, a complete and clean copy of data can be provided to restore the business system in a timely and effective manner.
As a data carrier, storage is the last line of defense for data security. HUAWEI OceanStor Pacific distributed storage aims at network threat attacks such as ransomware. Through data encryption, data tampering prevention, detection and analysis capabilities, the AirGap security isolation zone is introduced to prevent, perceive, and recover ransomware attacks on the storage side, greatly improving data resilience.
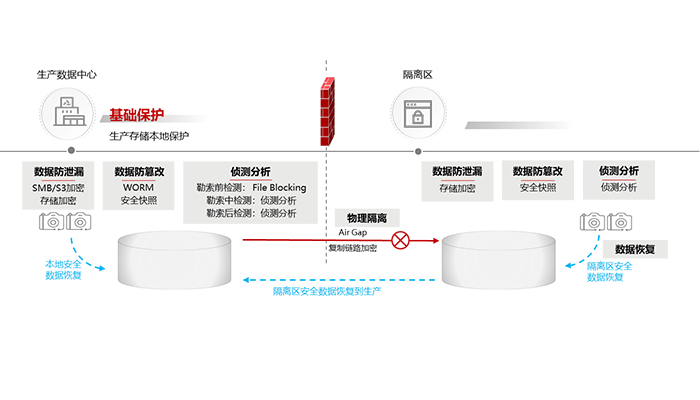
Next, let's take a look at some key technical points involved in Huawei's OceanStor Pacific distributed storage anti-ransomware solution.
Encryption is a typical method to prevent sensitive information from being leaked after raw data is stolen. If the data is encrypted, even if the hacker gets the data, it also protects the original information from being disclosed because it cannot be decrypted. OceanStor Pacific's data encryption includes storage encryption and transmission encryption. Storage encryption prevents physical attacks (such as storage theft and hard disk theft), while transmission encryption can effectively prevent data from being intercepted, stolen, leaked, and tampered with during transmission.
Anti-Tampering is an important part of the OceanStor Pacific storage anti-ransomware solution. It can prevent tampering in scenarios where unstructured data is written at one time and read multiple times, you can also prevent tampering at the snapshot level when modifying write scenarios.
Unstructured data WORM (Write Once Read Many) means that data can be written only Once and Read multiple times. You can set a protection period for files. During the protection period, files can only be Read, and cannot be modified or deleted, you can delete objects after the protection period expires.

The data in both a security snapshot and a normal snapshot is read-only. The biggest difference between the two is that the security snapshot has a retention period attribute after it is generated. During the retention period, even the administrator has no permission to delete the snapshot. After expiration, you can manually or automatically delete the security snapshot.
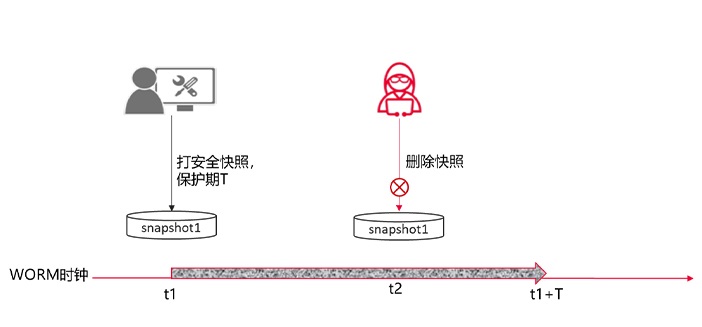
WORM clocks are used in both unstructured data worms and security snapshots. The WORM clock of the cluster can only be set once, and the WORM clock has the following characteristics: When the WORM clock is larger than the system clock, it is corrected to the system clock; The WORM clock is smaller than the system clock, the maximum number of WORM Time added per hour cannot exceed 138S. This prevents attackers from bypassing unstructured data worms and protecting security snapshots by modifying WORM clocks or system clocks.
Although OceanStor Pacific has the ability of unstructured data WORM to prevent data from being tampered with or deleted, some data needs to be modified in normal scenarios and WORM protection cannot be applied, only security snapshots can be used to protect data replicas from deletion. In the face of ransomware attacks, it is particularly important to timely perceive that data is encrypted by ransomware and ensure that a "clean" copy of data is available for recovery. Effective and timely detection and analysis of protected data can reduce the range of data encrypted by ransomware and improve the success rate of data recovery.
The blackmail software detection and analysis scheme combined by OceanStor Pacific & CyberEngine security integrated machine implements three layers of protection and detection before, during and after the Blackmail virus attack:
√ before attack (transmission stage): Intercept the writing of files with known Blackmail virus suffixes;
√ in attack (lateral shift and encryption stage): monitor the writing of known blackmail encrypted files, identify the IO behavior of Blackmail virus, and confirm whether blackmail is detected through machine learning model;
√ after the attack (blackmail completed): extract the snapshot change feature of the file system, identify it from the content perspective, and confirm whether it is blackmailed through the machine learning model.
Blackmail file interception is based on the FileBlocking function of OceanStor Pacific, which intercepts the behavior of Blackmail virus by intercepting the writing of encrypted files with known Blackmail virus.
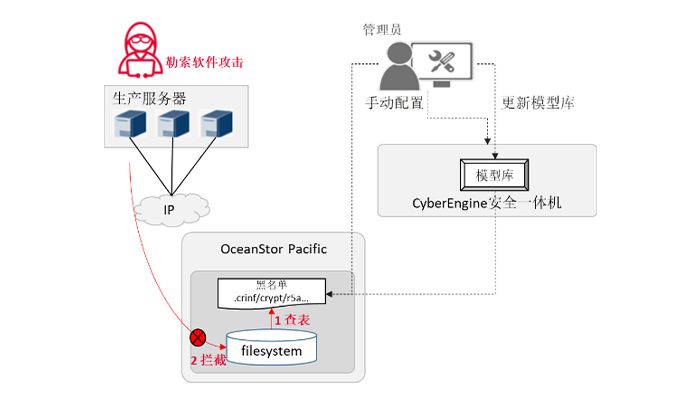
√ OceanStor Pacific saves a FileBlocking rule table in the access protocol configuration. You can set the rules to block files with a specific extension to prevent these files from being written to the storage system.
√ the CyberEngine security all-in-one machine presets the commonly used detection model, and the detection model presets the known blackmail file extension. You can import a detection model to update the blackmail file extension, or create a file extension filtering rule to add the blackmail file extension to be intercepted.
Blackmail virus attack vectors have common characteristics and are uniformly highly random read, encrypted, written and deleted, which is the theoretical basis for detecting the behavior of I/O pieces of blackmail soft anomalies;
√ it must read files, which is necessary to encrypt data.
√ it must write files. The number of write sections is similar to the number of read bytes. It can be a newly created file or rewrite the original file.
√ it must destroy the original information and delete or rewrite the original file.
√ read and write operations are similar in time or even parallel.
√ it wants to perform read/write and delete operations quickly.
In response to the commonality of ransomware attacks, OceanStor Pacific & CyberEngine builds abnormal I/O behavior indicators that reflect abnormal read and write behaviors and indicators that reflect encrypted and damaged files. The detection steps combining the fast screening of abnormal behaviors and the detection of deep detection of file damage are adopted in order to achieve the purpose of accurate detection of ransomware stored, and solve the high confidence level of ransomware detection in the existing storage system, wide coverage, strong timeliness, low resource overhead, and resistance to extreme attacks.

√ rapid screening of abnormal I/O behaviors
by analyzing the I/O behavior of the storage system and combining the abnormal I/O behavior characteristics, abnormal I/O behavior is identified. Perform deep file damage detection on files corresponding to abnormal I/O operations.
√ file damage depth detection
through the basic feature detection of file content, damaged files are identified. For files that do not have abnormal basic features, deep detection of file content is carried out based on machine learning algorithm, further check whether the file is damaged.
√ create a security snapshot and send an alert
create a security snapshot of the file system where the damaged file is located and send an alert to remind the Data Protection administrator to intervene in time to avoid further spread of the blackmail virus and reduce losses.
Once data in the system is encrypted by ransomware, it becomes particularly important to have a "clean" copy of data available for recovery. OceanStor Pacific & CyberEngine's periodic copy blackmail detection function allows you to set a daily or even hourly cycle to detect namespace snapshots and identify whether namespace data is infected by blackmail. If the data in the snapshot is secure, set this snapshot as a secure snapshot and become a clean and reliable recovery data source that will not be deleted by ransomware.
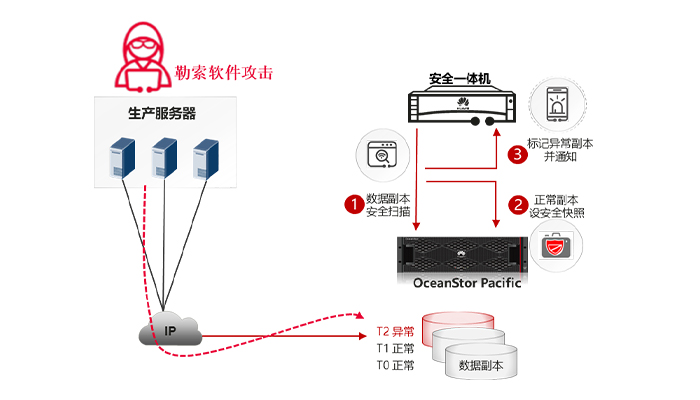
Snapshot blackmail detection includes:
√ detection of known blackmail features for a single snapshot
two common behaviors of blackmail virus: adding a suffix after an encrypted file and leaving a blackmail message file. For known blackmail viruses, traces of blackmail infection can be found through suffix and blackmail.
√ machine learning detection of data change behaviors before and after snapshots
firstly, based on the metadata features of the snapshot, several basic change features are quickly extracted to form a baseline model. Based on the baseline model, whether the changes of each subsequent snapshot are suspicious or not is determined. If a suspected infection is detected, the full change feature of the suspected snapshot is further calculated and extracted, and the machine learning model is used for detection.
Through data encryption, data tampering prevention, detection and analysis, and the AirGap to be introduced, Huawei OceanStor Pacific has built a long-standing missing data security protection layer in the traditional security defense system, let organizations and enterprises dare to say "no" to blackmail ". As the saying goes, the blackmail virus is constantly changing through iteration. HUAWEI OceanStor Pacific will continue to follow the development of the blackmail virus and optimize the plan to protect the data security of customers.
In today's era, the vitality of data is shining in various industries. Data productivity has become an indispensable force and become the engine and accelerator of world development. Huawei will continue to innovate and use technology to build protective walls to protect data security by means of data encryption, real-time ransomware detection, detection and analysis, and security snapshots, is to protect the healthy and stable sustainable development of all walks of life.
Disclaimer: the content and opinions of the article only represent the author's own views, for readers' reference of ideological collision and technical exchange, and are not used as the official basis for Huawei's products and technologies. For more information about Huawei's products and technologies, visit the product and technology introduction page or consult Huawei's personnel.


