According to third-party statistics, up to 35.83 million ransomware attacks occurred in the whole network in 2022, an increase of more than 13 million times compared with 2021. There is no lack of large-scale vicious blackmail incidents.
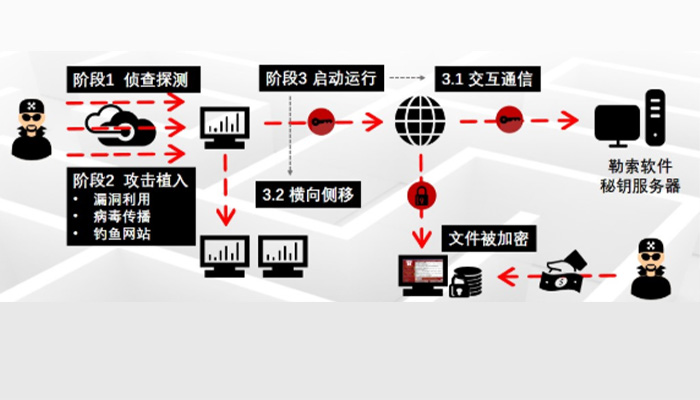
The attack process of ransomware usually has the following stages:
2. Attack implantation (Transmission Stage)
at this stage, attackers may send virus-containing emails or phishing websites to targeted email addresses or other facilities, or exploit vulnerabilities discovered by scanning, A ransomware virus is implanted into the target production host or storage system.
After the blackmail is implemented, an obvious prompt will be given to the target to ask for ransom.
1) effectively prevent data from being encrypted;
2) timely warning of ransomware attacks;
3) after data is encrypted, a complete and clean copy of data can be provided to restore the business system in a timely and effective manner.
Next, let's take a look at some key technical points involved in Huawei's OceanStor Pacific distributed storage anti-ransomware solution.
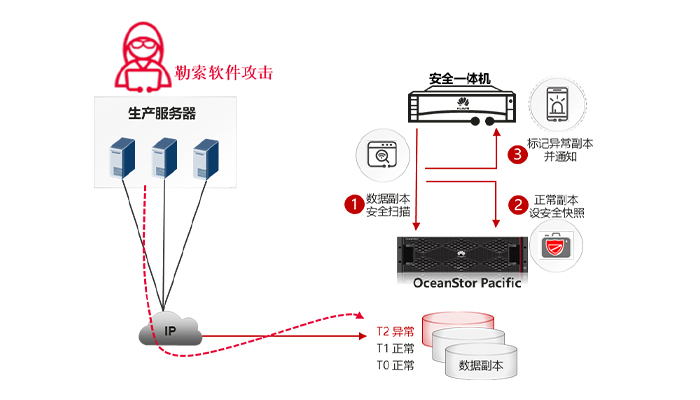
Anti-Tampering is an important part of the OceanStor Pacific storage anti-ransomware solution. It can prevent tampering in scenarios where unstructured data is written at one time and read multiple times, you can also prevent tampering at the snapshot level when modifying write scenarios.
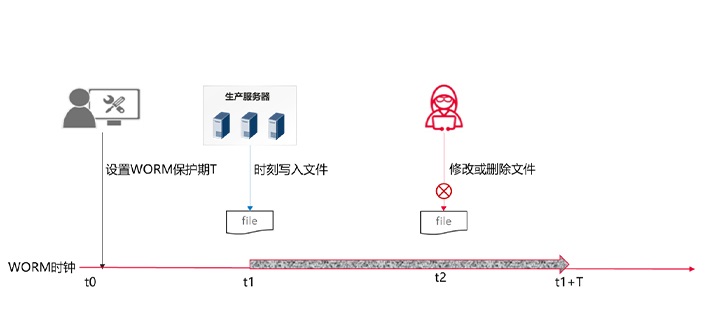
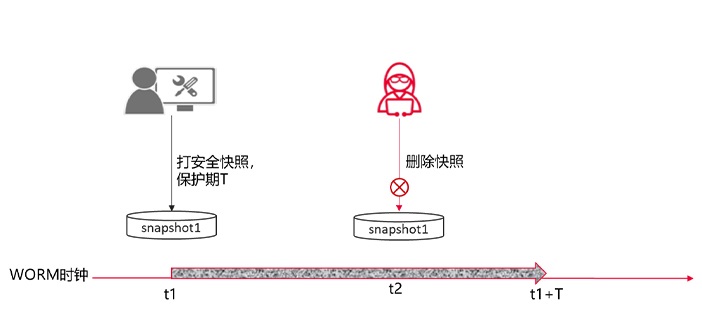
although OceanStor Pacific has the ability of unstructured data WORM to prevent data from being tampered with or deleted, some data needs to be modified in normal scenarios and WORM protection cannot be applied, only security snapshots can be used to protect data replicas from deletion. In the face of ransomware attacks, it is particularly important to detect that data is encrypted by ransomware in a timely manner, and ensure that a copy of data of & ldquo; Clean & rdquo; Can be used for recovery. Effective and timely detection and analysis of protected data can reduce the range of data encrypted by ransomware and improve the success rate of data recovery.
& radic; Before attack (transmission stage): Intercept the writing of files with known Blackmail virus suffixes;
& radic; Attack (lateral shift and encryption stage): monitor the writing of known types of blackmail encrypted files, identify the IO behavior of Blackmail virus, and confirm whether blackmail is detected through machine learning model;
& radic; After the attack (blackmail completed): extract the snapshot change feature of the file system, identify it from the content perspective, and confirm whether it is blackmailed through the machine learning model.
& radic; OceanStor Pacific stores a FileBlocking rule table in the access protocol configuration, which allows you to block specific operations on files with a specific extension to prevent these files from being written to the storage system.
& radic; The CyberEngine security all-in-one machine presets the commonly used detection model, and the detection model presets the known blackmail file extension. You can import a detection model to update the blackmail file extension, or create a file extension filtering rule to add the blackmail file extension to be intercepted.
& radic; It must read files, which is necessary to encrypt data.
& radic; It must write files. The number of write sections is similar to the number of read bytes. It can be a newly created file or rewrite the original file.
& radic; It must destroy the original information, delete or rewrite the original file.
& radic; Read and write operations are close to or even parallel in time.
& radic; It wants to perform read/write and delete operations quickly.
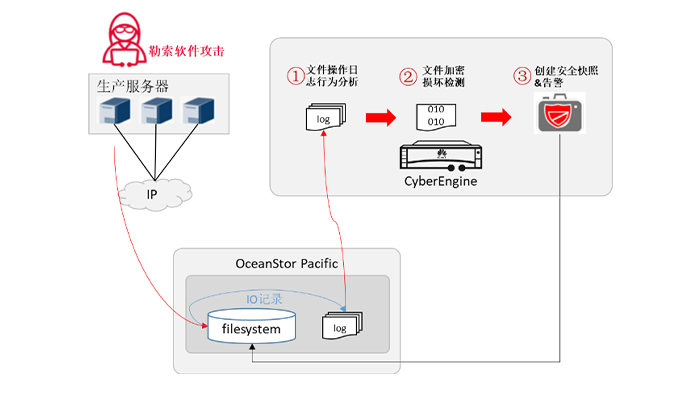
Once data in the system is encrypted by the Blackmail virus, it becomes particularly important to have a copy of the data of & ldquo; Clean & rdquo; For recovery. OceanStor Pacific & CyberEngine's periodic copy blackmail detection function allows you to set a daily or even hourly cycle to detect namespace snapshots and identify whether namespace data is infected by blackmail. If the data in the snapshot is secure, set this snapshot as a secure snapshot and become a reliable recovery data source that will not be deleted by ransomware.
& radic; Detection of known blackmail features for a single snapshot
two common behaviors of blackmail virus: adding a suffix after an encrypted file and leaving a blackmail message file. For known blackmail viruses, traces of blackmail infection can be found through suffix and blackmail.
& radic; Machine learning detection of data change behavior before and after snapshots
firstly, based on the metadata features of the snapshot, several basic change features are quickly extracted to form a baseline model. Based on the baseline model, whether the changes of each subsequent snapshot are suspicious or not is determined. If a suspected infection is detected, the full change feature of the suspected snapshot is further calculated and extracted, and the machine learning model is used for detection.
In today's era, the vitality of data is shining in various industries. Data productivity has become an indispensable force and become the engine and accelerator of world development. Huawei will continue to innovate and use technology to build protective walls to protect data security by means of data encryption, real-time ransomware detection, detection and analysis, and security snapshots, is to protect the healthy and stable sustainable development of all walks of life.


 Reprint
Reprint